Audit logs
This section explains what audit logs are and their uses.
Audit logs are essential records that track every activity performed within your Quickwork account. They provide a detailed account of operations on various components, such as journeys, folders, and connections, performed by users and teams. By capturing details like user actions, timestamps, IP addresses, and system information, audit logs help monitor and audit activities, ensure transparency, and maintain security.
✅ Prerequisites
- Basic understanding of Quickwork terminologies and familiarity with Quickwork's GUI.
- Understanding the basic principles of automation, including triggers, actions, and the concept of automated journeys.
Viewing audit logs
-
To view the audit logs, log into your Quickwork account.
-
Navigate to the Dashboard tab.
-
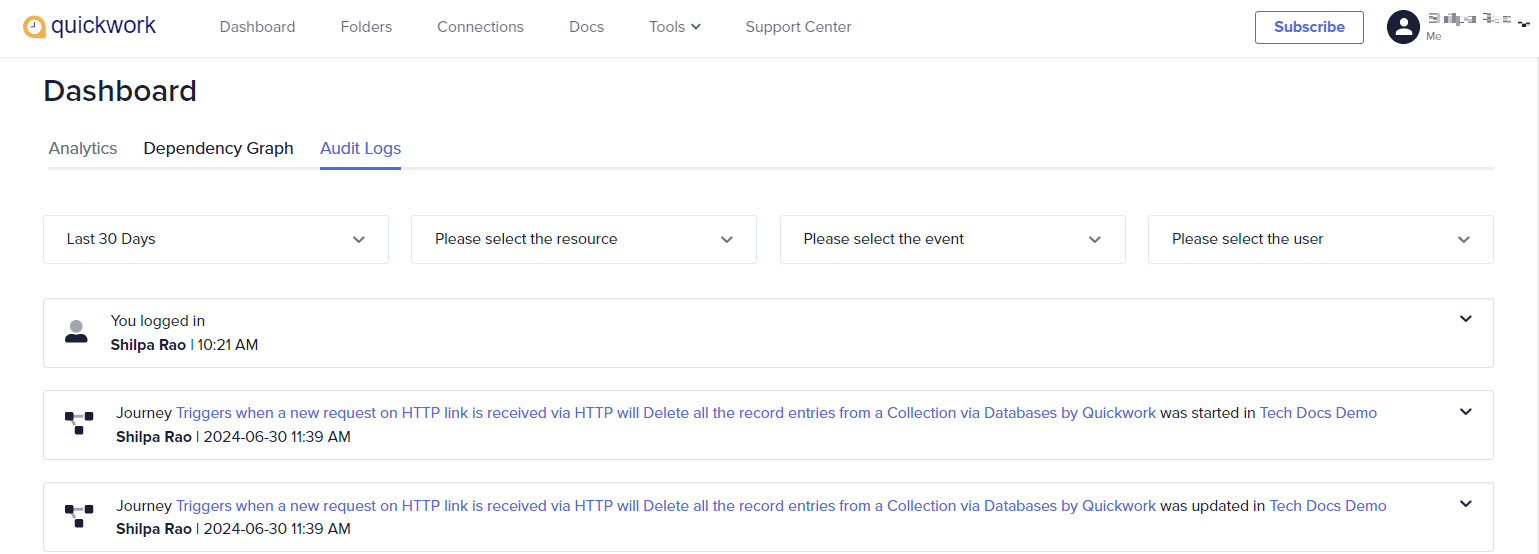
Click on the Audit Logs tab. The details appear with a default timestamp filter set to the Last 30 days.
Filtering the audit logs
- To get more granular insights, you can filter the audit logs based on:
-
Duration: Select the time range for which you want to view the logs. You can choose from the last 1 hour, last 24 hours, last 7 days, or last 30 days.
-
Resource: You can choose the resource for which you want to see the specific logs. You can select journeys, folders, connections, a user, team, or a notification email.
-
Event: You can filter logs based on specific events associated with the selected resource (For example, if resource is Journey, events are journey creation, updation, cloning, starting, stopping, moving, or deletion).
-
User: You can view logs for actions performed by a specific user in your team.
-
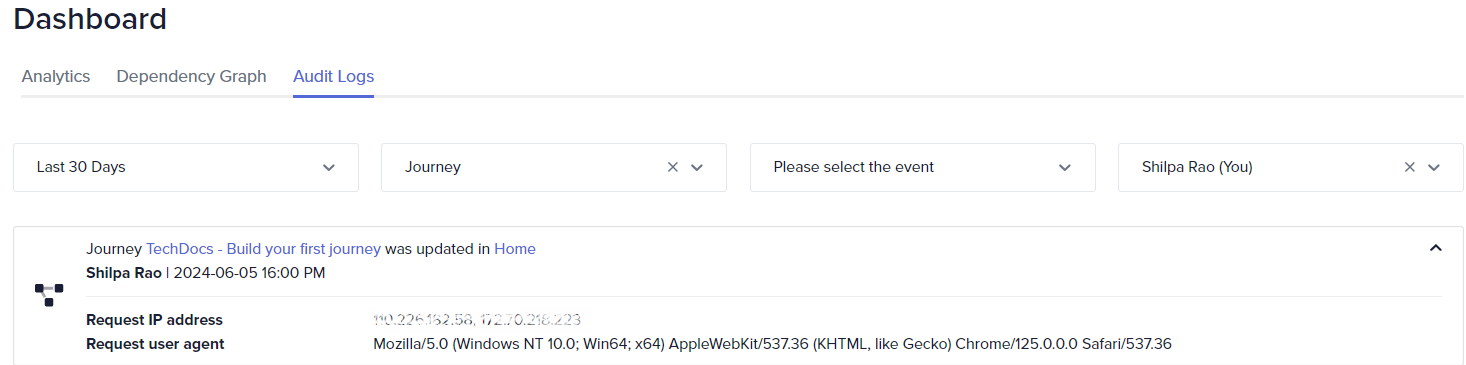
Sample audit log
Each audit log entry includes the following information:
-
Action performed: Describes the action taken on the journey (based on the selected event). For example, Journey TechDocs - Build your first journey was updated in the Home folder.
-
User name: Identifies the user who performed the action.
-
Timestamp: The date and time when the action occurred.
-
Request IP address: The IP address of the system used to perform the action.
-
Request user agent: The system information or details about the browser and operating system used.
✏️ Tips and recommendations
- If there's suspicious activity, use the IP address and user agent information to trace the source of actions, which can help in identifying unauthorized access or potential security breaches.
- Schedule regular reviews of your audit logs to catch anomalies early. This practice helps in maintaining security and compliance.
📚 Additional resources
Updated 3 months ago
